Клавиатурный шпион: лучшие программы для слежки
Содержание:
- Home Keylogger
- Logs delivery
- Spyrix Employee Monitoring for Mac — Main Features
- Recording Features
- Keylogger (keystrokes logging)
- Screenshots capture
- Snapshots from web camera
- Hidden recording from microphone
- Hidden recording from web camera
- Websites
- Search Engines Monitoring
- Application Activity
- Domain users monitoring
- Geolocation tracker
- Facebook Activity
- LinkedIn Activity
- Social Activity
- Skype
- Popular IM Messengers Activity
- Employee activity
- Printer Control
- Removable Drives Control
- Methods of data viewing
- Recording Features
- Kidlogger
- Top reasons to start using Ardamax Keylogger
- Ardamax Keylogger | $49 | Win
- All In One Keylogger
- What is a keylogger?
- Do mobile devices get keyloggers?
- Legal software products for computer monitoring
- mSpy: Best Android keylogger
- Actual Keylogger
- Is Keylogger Legal? If It Is, Under What Circumstances?
- The working principles of software keyloggers
- Key Features
- PC Monitoring
- Hidden Mode
- Report Viewer
- what is monitored
- What is it for
- Kidlogger Free | Free | Win, Mac, Android & iOS
- Best Free Keylogger
- Why is IwantSoft the best?
- Особенности выбора
Home Keylogger
Home Keylogger is a free keylogging software designed to intercept and record in a file, everything entered from the keyboard. This keylogger works in the hidden mode and becomes visible only when you (the installer) enter a pre-set combination of keys.
Main features of Home Keylogger:
- Ease-of-use
- Small and compact, using minimal system resources
- Invisible to everyone except installer of the program (You).
- Quick access to keyboard logfile: – just double click on tray icon.
Abilities of Home Keylogger:
This free keylogger tells you:
- What was typed,
- When it was typed,
- In what program it was typed, and
- On what web site it was typed.
Home Keylogger is a little jewel of a keylogger program which will endear itself to users because of simple yet elegant interface, smooth functioning, and legible display of user actions. And best of all, Home Keylogger is FREE. Download Home Keylogger.
Logs delivery
5.1 Web log delivery

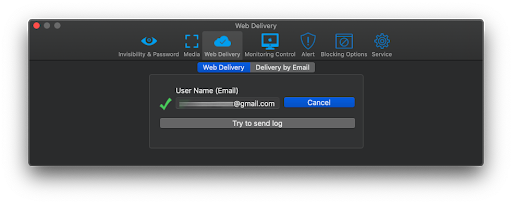
3) If you did everything correctly, you will see this message:

4) Test log delivery with “Try to send log” button. Then you can close the settings.
5) In a few moments, you will see the first data in your account here: . Do not forget to refresh the page.

5.2 Email log delivery
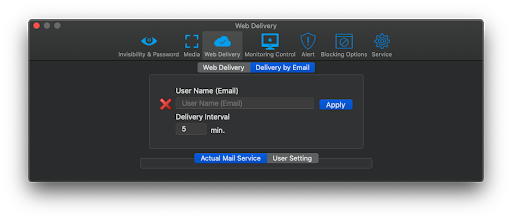
2) To set up delivery via your mail service, go to the tab “User Settings” and fill in the fields:
- Your “User Name (Email)” is your email address;
- SMTP Server and SMTP/Port can always be found in your email provider support or knowledge base;
- User name – on most email services, it is usually your full email address (but some services use the email without the part that comes after @);
- Password is your email password.
Click “Apply”.
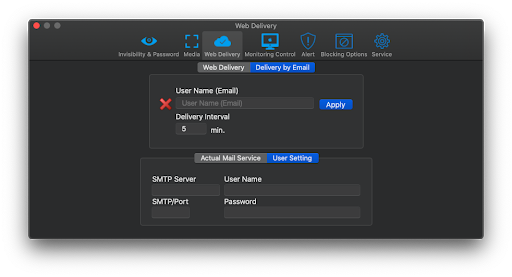
3) If you did everything correctly, you will see this message:

5.3 Email log delivery for Gmail users
1) Open google.com and go to your account settings.

2) Click “Manage your data&personalization” in Privacy&Personalization.

3) Go to “Security” and scroll down to “Less secure app access”. Click “Turn on access”.

4) Click the slider button “Allow less secure apps”.

Spyrix Employee Monitoring for Mac — Main Features
Recording Features
-
Keylogger (keystrokes logging)
With the keystrokes logger, you can see all the keystrokes that are made on your computer, even if they have been removed. Except passwords.
-
Screenshots capture
It takes screenshot of the desktop view without the user knowing it.
-
Snapshots from web camera
Snapshots are made on remote request from web or according to settings
-
Hidden recording from microphone
Audio recording is made on remote request or on exceed of chosen microphone level
-
Hidden recording from web camera
Video recording is made on remote request
-
Websites
Collecting of data about all visited websites
-
Search Engines Monitoring
Records the searches that are carried on search engines such as Google, Bing, Yahoo and AOL. This includes recording of keywords that are used for making the searches.
-
Application Activity
Collecting of data about running applications (time of launch/close, duration of usage)
-
Domain users monitoring
Activity monitoring of domain users in corporate networks
-
Geolocation tracker
-
Facebook Activity
Collecting of data about Facebook chats, visited pages, search queries, etc
-
LinkedIn Activity
Detailed monitoring of activity in business-oriented social network LinkedIn
-
Social Activity
Besides Facebook и LinkedIn, you will be able to control activity in popular social networks like Myspace, Twitter, Google+, VKontakte, Odnoklassniki
-
Skype
Two-way dialogue interception
-
Popular IM Messengers Activity
It monitors the activities of more than 20 renowned Messengers such as MSN and ICQ.
-
Employee activity
Beginning and end of the work with the computer, the idle time
-
Printer Control
This program also has the trait of Printer Control which allows controlling the printer activities on the system.
-
Removable Drives Control
The activities of removable drives such as HDD, USB and SD can be both monitored and controlled.
Methods of data viewing
-
Online via secure web account
You will get access for viewing collected data in your account on dashboard.spyrix.com
-
Live Panel
Viewing of all employees’ screens simultaneously in real time
-
Live Viewing
Watching the screen in live mode
-
Remotely via sending log to your email, FTP, LAN
-
Remotely via cloud storage: Google Drive
You may configure sending regular logs to cloud storage
-
Locally, on employee’s computer
You may view collected data directly on employee’s computer. Access to collected data can be closed with a password that will be available only for a director
Kidlogger
Kidlogger is a very simple keystroke logger program, designed for home family users, and intended to keep watch on kids’ (2-7 years old) activity on the computer. A better way to control online activity of kids of that age group is to use Kidzui.
Benefits of Kidlogger Keylogger:
- It records in a logfile, all websites visited, chat rooms talks, programs run, documents and windows opened, and movies and shows viewed.
- It is a simple and free keylogger and activity monitoring program meeting family requirements.
Kidlogger Features and Functionalities:
- Recording of all keystrokes.
- Monitoring and Recording of instant messenger chats, online chats and emails.
- Kidlogger starts in invisible mode at system startup.
- Monitoring of Multiple Users supported.
- Kidlogger monitors and logs all applications, and captures screenshots. It also records the text typed in these applications, displays the exact time, date and active window title of the programs launched on your computer. Kid-logger also captures, at 15-minute intervals, all screen contents into a BMP file for you to see.
- User-friendly Log files containing all captured data, and named by date, are sent to you by email.
- Kidlogger is a free and open source keylogger (keystroke logger) program designed for first-time users.
Also check out:
- 5 Best Free Firewall Software
- 5 Free Software to Remotely Connect to Your Computer
Top reasons to start using Ardamax Keylogger
Protect your children online
The web these days of full of dangers and inappropriate content that is just a few clicks away. You cannot really hide all of this from your kids, but you can definitely break a habit before it becomes an obsession or make sure that your kid is not chatting with dangerous “buddies”, who can be anyone: from robbers or perverts to recruiters for radical terrorist groups. The more you know about your kids, the better you are prepared to get them out of trouble or prevent it altogether.
Catch your cheating partner
Online dating is huge nowadays, and it’s never been easier to start an online affair that can easily materialize in the real world. Eavesdropping on your partner of spouse is irrefutably bad, but if you have a solid reason to suspect that your significant other may me involved into something, it never hurts to check. This way, you can dot the I’s and make the right decision long before its way too late and this situation delivers its crushing blow.
Back up and recover lost text entries
Ironically, a key logger can be used not only as spy software, but also as a tool that constantly records all text entries and can, if and when necessary, restore them. Ardamax Keylogger will help you restore a previously entered, but forgotten password, address, name or even text fragments that were lost after a system crash or abrupt program termination. When this keylogger is enabled, your backup tool is always on, too.
Monitor your employees’ activities
Employee monitoring is one of the most traditional purposes of spy software. Knowing what your employees do on their workstations can potentially prevent a number of serious problems, from data leaks and commercial espionage to losing your key team players to competitors. With Ardamax Keylogger installed on employees’ computers, you will always be able to quickly run checks on suspicious individuals and take preemptive action.
Ardamax Keylogger | $49 | Win
Ardamax Keylogger is a small and easy to use keylogger which records every user activity and saves data in the log file. The admin can look into the log file in text or web page format. This tool will tell you about every activity on the computer while you were away.
- Pressed keys recording: it includes all pressed keys, entered passwords, and hidden symbols
- Browser history
- All opened web page logging
- Web Camera recording
- The program records screenshots and saves them in logs here and then
- Logs are sent via email
In every given time the keylogger can send recorded logs, which is quite useful for remote monitoring.
- Microphone Recording. Voice recording through a microphone with audio file compression in real time.
- Visual monitoring. Screenshots are being done at regular intervals and saved in log files.
- Chat monitoring. Ardamax Keylogger was developed for recording and monitoring chats on both sides (Skype, Yahoo Messenger, or Google).
All In One Keylogger
Price: 7-day Free trial; Pro version costs $69.95System requirements: Windows XP/Vista/7/8/10 32bit or 64bitDownload Free version: http://www.softpedia.com/
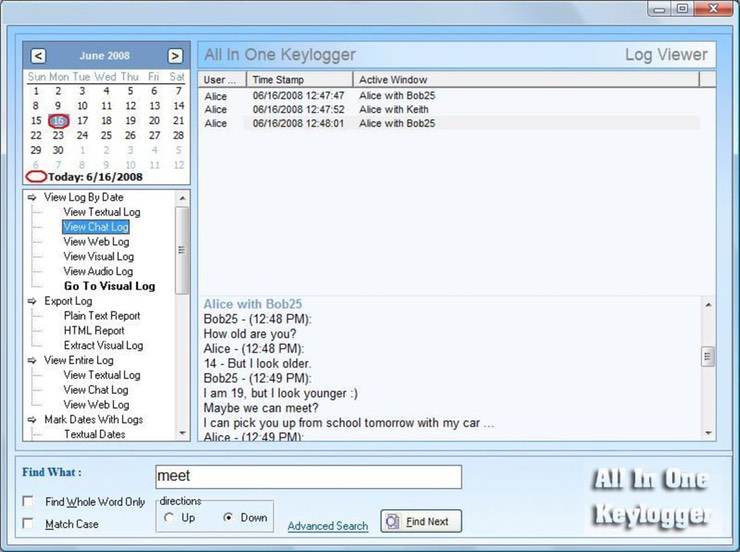
If you’re looking for a free keystroke logger with virtually all logging and surveillance features imaginable, you should give All In One Keylogger Keylogger a try. This feature-packed Windows 10 keylogger can record all the applications running on a computer as well as record text that was copied to the clipboard, capture both sides of internet conversations, take screenshots, record audio using the microphone, take pictures from the webcam, save the names of the printed documents, and so much more. However, there’s a price to pay for having so many features in one app, and that price comes in the form of hard-to-navigate user interface.
What is a keylogger?
A keylogger is a type of monitoring software. It will track everything the phone’s user types and store it on an external server. That means you will know everything he or she types on chat apps, social media or tinder, but also URLs typed in, passwords, numbers and anything else. Usually, keylogger apps come with a plethora of other spy features or parental control features. The keylogger is often one of the dozens of other monitoring options. Besides simply monitoring keystrokes, they can also give you access to messages received through chat apps. You will be able to track the phone’s location, calls, browsing history, installed apps, and so much more.
Do mobile devices get keyloggers?
First the good news. There are no known hardware keyloggers for mobile phones. But both Androids and iPhones are still vulnerable to software keyloggers. There are claims out there that, because the mobile device’s screen is used as a virtual keyboard for input, keylogging is not possible. But you have only to search for smartphone keyloggers to see how many are available for download. Be assured that such keyloggers can capture what screens are pressed, so they see and record what virtual buttons the user touches.
As for infection methods, anyone who has temporary sneaky access to the phone without the user’s knowledge can load a keylogger. And just like it is with PC and Mac laptops, tablets, and computers, smartphone users can infect themselves if they fall prey to phishing expeditions, or unwisely click on an attachment of uncertain provenance.
Legal software products for computer monitoring
The majority of the modern legal keyloggers are intended for:
- parents (parental control): monitoring online activity of their children and getting notifications in case they make attempts to visit adult sites or launch any of the prohibited programs;
- security team of the company (employee monitoring): monitoring improper PC use, use of workplace computer outside of working hours, control over keystrokes containing commercially sensitive words, disclosure of which could lead to losses;
- private individuals (PC monitoring software): PC usage analysis in case someone else except the owner has access to this device;
- jealous spouse (spouse monitoring): keeping an eye on online actions of the spouse, proving or rejecting any suspicions about “virtual” or real breach of faith;
- different security polices: analysis and investigation of various incidents connected with PC usage.
mSpy: Best Android keylogger
https://youtube.com/watch?v=alCjwqLbOj0
https://youtube.com/watch?v=alCjwqLbOj0
mSpy is a hidden keylogger for Android. It will monitor everything typed in any Android device from Android 4.0 and higher. It will all you to track all chats, including messages sent or received using Facebook Messenger, Snapchat, WhatsApp, Viber, Tinder, and more. That way, you will know exactly what your child, spouse, or employee is talking about and with whom. You can also use it to get logins, URLs typed, and more.
mSpy costs just $16.66 per month.
Why choose mSpy?
mSPy is the industry leader and has the best keylogger for Android. The app is secure, hidden, and discreet, so the phone’s user will never know it is there. Besides the features listed above, mSpy is the only app that offers the following:
- Remote control access
- 30-day money-back guarantee
- 24/7 multi-language support
Besides mSpy, we have also listed two other best Android keylogger apps. These apps also have plenty to offer when it comes to spying on Android.
Actual Keylogger
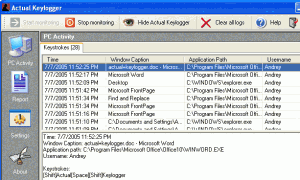
Need to track down a person’s keystrokes:
Systems and business administrators who are biting their nails, worried about leakage of vital confidential information by an employee, parents who are anxious about their children’s safety on the internet, and internet café owners, who are responsible for regulating ‘clean’ browsing by their customers – all these people need an instrument to know for certain, the web browsing activities of their employee, child, or customer respectively. Only then they would be in a position to take suitable legal, disciplinary or remedial action. This is where Actual Keylogger comes in.
How does Actual Keylogger works:
Actual Keylogger is a free keylogger software that runs inconspicuously in the background, automatically recording every user keystroke, including special and function keys. It records the name and duration of every website visited, the exact keystrokes made, encrypts and enters the information in a log file, which cannot be seen by anyone except the installer of this program. The log file displays:
- Websites visited with time-stamp.
- All typed matter
- Money transacted online
- Email, chats
- CD/DVDs copied
Features of Actual Keylogger:
Actual Keylogger has following features and functionalities:
- Password Protection
- Logfile Encryption
- Viewing Reports: choice between HTML and plain TEXT.
- “HIDDEN” Mode Option (to stay invisible for the user)
- Only the person with a special key combination (installer) can control Actual Keylogger.
You can also hide the installation folder of Actual Keylogger, disable its entry in the Add/Remove Programs dialog box and hide its shortcuts. Choosing the “HIDDEN” mode option makes it invisible, irrespective of the operating system. It is also undetectable by Antivirus software.
Actual Keylogger provides you with detailed information about all the activities going on in your computer, and best of all – it’s Free! Download Actual KeyLogger.
Is Keylogger Legal? If It Is, Under What Circumstances?
Are keylogger legal? Keylogger is illegal if it is installed on computer not owned by you, especially the intention is to steal credit cards, passwords and private information. Keylogger is ideal for:
- Parents concerned about the kind of programs their children might be running and the sites they might be visiting on the Internet.
- System administrators wanting to know exactly what has taken place on the system.
- CEOs checking the time spent by employees on non-work or other tasks. Actual Keylogger provides you with full control over your company’s computers.
- Computer teachers and Internet café owners who want greater insight into what their users have been doing.
Note: In some countries such as Germany, it is required by law to inform your employee that a key monitoring software is installed. Can Keylogger be installed remotely? No, you need physical access to the computer, unless there is a bug or you work in the NSA.
The working principles of software keyloggers
Keylogger software can use various methods of capturing keystrokes made by the certain user.
Keyboard interception (so called hook)
In the Windows environment, ‘hook’ means interception of the system messages, using Win32Api programming element. The most keyloggers use WH_Keyboard hook as a basis, while WH_JOURNALRECORD hook is used less frequently. The difference consists in that WH_JOURNALRECORD doesn`t depend on Dynamic Link Libraries (DLLs).
Keyboard state polling
A quite simple method that doesn’t require implementing the program in a graphical interface of the system. However, its serious drawback is high resource consumption. This disadvantage leads to the activation of antivirus and antispyware software.
Rootkit intruders
They penetrate into csrss.exe process and intercept all data during exchange between keystrokes and this very process. In most cases, even when Windows onscreen keyboard is used (which is highly recommended against data theft), the data are intercepted by this type of keylogger.
Key Features
PC Monitoring
Free Keylogger discreetly monitors all activities on your computer including keystrokes, program usage, visited websites, and so on.
Hidden Mode
The keystroke logger remains invisible to users, and only the owner can press a secret hotkey and enter a password to make it visible again.
Report Viewer
The software provides an easy to use yet powerful report viewer. It allows you to get detailed info about every activity, as well as a general statistics.
what is monitored
- Keystrokes
- Used applications
- Copied text
- Visited websites
- Activity in social networks
- Instant messages (Skype etc.)
- Operations with USB devices
- File operations in folders
- Documents sent to print
- E-mail attachements
- Files uploaded to Internet
- Screen capture
- Snapshots from webcam
- Sound from microphone

What is it for
Iwantsoft Free Keylogger discreetly monitors nearly all activities on a computer by registering every keystroke, capturing the content of the system clipboard, logging program usage, keeping track of visited websites and recording chats in messengers and social networks. Other activities are also recorded.
The program is equally suitable for home and work use. At home, it can be used by parents looking to identify potential threats to their children. At work it may be interested for employers making sure their business secrets are not leaked to competitors.
Softonic
Techulator
DownloadSource
Here are the three main advantages of our keystroke logger software over competitors:
1.
Unrivaled functionality. This is a powerful all-in-one monitoring software. In addition to standard keylogging function, the software impresses with a huge set of advanced monitoring, notification and filtering features.
2.
Quick installation builder. Our program allows you to create a preconfigured installer. This installer should be run once on the target computer. The entire installation and configuration process will go in automatic mode.
3.
Unlike other keyloggers, Iwantsoft Free Keylogger is equally well suited for use both at home and at work. For use in the companies there are additional tools for monitoring, collecting statistics, and control.
Kidlogger Free | Free | Win, Mac, Android & iOS

Parental control feature helps to protect children in the internet environment. You can find out about your child’s online life, and who they talk to in particular. Moreover, an employer, armed with this software, can monitor personnel activity and discipline them in this way. It is like a personal automated journal.
What is monitored:
- Laptop or phone location through GPS
- Pressed keys
- Screenshots saving
- Web history monitoring
- Calls recording (for Windows)
- Time-tracking
- Chat monitoring (Windows and Mac)
- Phone location tracking (Android, iOS, BlackBerry, MAC OS X), GPS or WiFi coordinates
- SMS (Android, Nokia, BlackBerry). All the inbound/outbound messages with names are tracked.
Best Free Keylogger
So, you will need to know what to avoid in an office workstation.
Why is it Necessary?
Keylogging helps big MNC’s to track their employees work progress on a daily basis. This cannot be done manually due to the employee count. Parents use it to keep a track of their child’s online activity too.
Unfortunately, keyloggers can be embedded in spyware allowing your information to be leaked to an unknown third party.
Hardware and Software Keyloggers
Keylogging can be done in two ways, hardware, and software. Hardware keylogging is just like a pen drive device attached to the USB of a keyboard and then connected to the system. You will usually find it in browsing centers.
Software keylogging is basically a code installed in a system and is difficult to find. Since they can be embedded to any spyware, things will be difficult to undo once your personal credentials are leaked to a third party.
Features
There are tons of features of a keylogger. We will mention a few important ones here as they are self-explanatory.
- All applications keylogger
- Weblogging
- Chat logging
- Screenshot logging
- Microphone logging
- Webcam logging
- Printer logging
- Files and Directories change logging
- Remote access logging
- Disable anti-keylogger software
- Log files Encryption
- Privacy features
- Password Protection
- Multilanguage-Localized keylogger
You can use this code or hardware for almost any application for your system. You can monitor your work even if you are on a vacation by using this software. It offers excellent flexibility and convenience.
Uses
Keyloggers can be used in various circumstances and almost everywhere. You will need to be smart enough to exploit its features mentioned above.
Here are a few uses of keyloggers:
- Monitoring employees and kids
- Listing the most used application and websites
- Workplace productivity tracking
- Most used contacts on phone (Calls, SMS, chats, and emails)
- Tracking phones
- System and phone remote surveillance
- Concerned security departments of the government can use it to spy on digital criminal activities
- It works both ways since illegal people can use the software to hack into government firms to obtain valuable information.
Various Keylogger Software
Before we talk about the various keylogger software available, we would like to inform you about a few things that will be useful for you once you start using the software.
Using a keylogger will help you find your children in case of an emergency, protect them from online predators and limit the sharing of information online. If you install a keylogger on a computer not owned by you, you will be penalized legally. So, you need to be careful while using this software. We would recommend you to use it for personal use only.
Why is IwantSoft the best?
Here are the three main advantages of our keystroke logger software over competitors:
1.
Unrivaled functionality. This is a powerful all-in-one monitoring software. In addition to standard keylogging function, the software impresses with a huge set of advanced monitoring, notification and filtering features.
2.
Quick installation builder. Our program allows you to create a preconfigured installer. This installer should be run once on the target computer. The entire installation and configuration process will go in automatic mode.
3.
Unlike other keyloggers, Iwantsoft Free Keylogger is equally well suited for use both at home and at work. For use in the companies there are additional tools for monitoring, collecting statistics, and control.
Особенности выбора
Рассматривая возможность установки такой программы, стоит знать, что некоторые утилиты показывают все, что было написано на клавиатуре. Другие же записывают информацию только с браузера или одного приложения, которое выберет пользователь.
Кроме того, есть утилиты с гибкими настройками, где можно подключать и отключать запись, а также есть те, в которых это невозможно регулировать.
Программы для слежки за клавиатурой отличаются друг от друга тем, насколько они открыты для пользователя. Варианты попроще очевидны, ведь в результате их деятельности файл с записью сохраняется на рабочий стол, где его сложно не заметить. Они подойдут для того, чтобы контролировать маленьких детей.
Другие утилиты работают скрытно, запись сохраняется в секретной папке или приходит пользователю на почту. Подобные утилиты нужны для того, чтобы факт слежки остался незаметным. Их устанавливают для контроля подростков или для того, чтобы убедиться в безопасности своих файлов на рабочем компьютере.
Есть платные утилиты — у них более широкий функционал, а также бесплатные версии. Учитывая то, сколько есть производителей подобного софта, а также то, как много показателей нужно учесть перед тем, как устанавливать программу, выбор кажется очень сложным.